How scam-proof are you really? These are the signs to look for and best strategies for combating the scam epidemic.
In the lands of cybersecurity, being “pretty sure” is pretty dangerous. Like many of us, Sarah considered herself tech-savvy since she used a computer daily for work, shopped online regularly, and even helped her parents set up their smart TV. So when she received an email from her bank about a suspicious transaction, she didn’t think twice about clicking the link to verify her account.
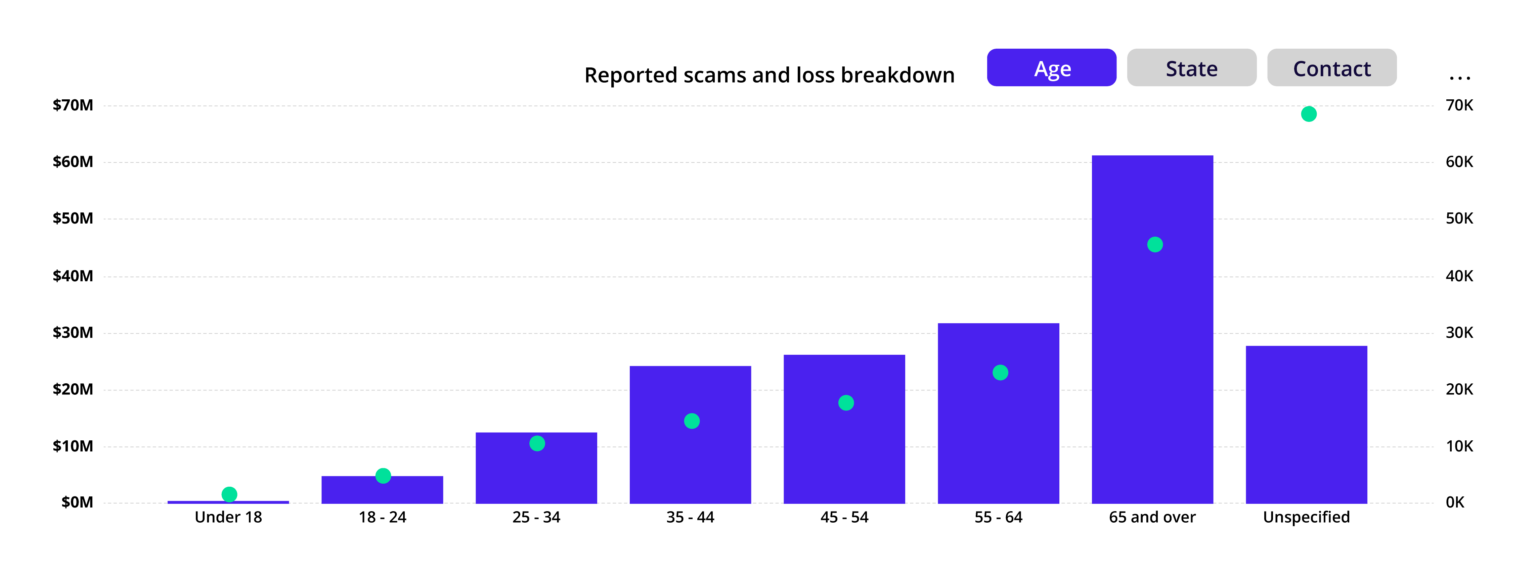
Little did Sarah know that single click would turn her life upside down for months. Hours on the phone to the bank, providing proof and the unknown of who else could have her information now. Stories like this are becoming alarmingly common, with investment, romance, and phishing scams ranking highest in Australia.
Most common types of online scams
When in doubt, reach out. If something seems off, always contact the company directly through their official channels, not the details in the suspicious message. Here’s what to look out for:
- Phishing emails: Use urgency and personalisation to trick people into revealing sensitive information.
- Fake online dating profiles: Build relationships and eventually ask for money. Be cautious if they refuse to meet in person or request payments through gift cards, wire transfers, or cryptocurrency.
- Fake tech support: Scammers claim your device has been compromised to gain remote access or sell unnecessary services.
- Fake shopping sites: They mimic real retailers, taking money and personal information. Be wary of deals that seem too good to be true and verify the site’s legitimacy.
- Investment/crypto scams: Be wary of opportunities promising high, fast returns with little risk.
High-profile hacks: The domino effect of data breaches
Considered the largest data breach in Australia to date, a 2022 breach affected up to 9.8 million Optus customers — nearly 40% of Australia’s population. If you weren’t affected, chances are someone you know was.
Hackers also hit Medibank, accessing 9.7 million customers’ details. In the US, T-Mobile exposed 76.6 million residents’ information, leading to a $500 million class action lawsuit. Even Uber’s systems were hacked, exposing internal communications.
How do hackers get into company systems?
- Outdated software leaving vulnerabilities unpatched.
- Improper security setups.
- Phishing attacks on employees.
- Poor encryption practices.
- Targeting less-secure third-party vendors.
Major organisations hit by ransomware attacks
Ransomware attacks encrypt files or lock victims out of their systems, demanding a ransom in cryptocurrency. Notable incidents include:
- Colonial Pipeline (2021): The largest fuel pipeline in the U.S. was shut down, paying $4.4 million in ransom.
- JBS Foods: Paid $11 million to recover from an attack that affected operations globally.
- Scripps Health: Hack shut down operations for weeks, costing an estimated $112.7 million.
Even the famous aren’t safe
Hackers compromised Chris Hemsworth’s account in 2020 as part of a Twitter hack targeting high-profile users. Hackers also accessed Selena Gomez’s Instagram in 2017, posting private content before security was restored.
What to do if you’ve been scammed or hacked
If those with teams of experts can fall victim, we must all remain vigilant. Here’s what to do:
- Change passwords for all affected accounts immediately.
- Contact your bank to prevent unauthorised transactions.
- Collect evidence like emails and screenshots.
- Run antivirus scans on your devices and update all software.
- Inform your contacts to prevent the scam from spreading.
Reporting scams to relevant authorities
- ScamWatch (run by the ACCC)
- Australian Cybercrime Online Reporting Network (ACORN)
- IDCARE for support to Australian victims
- The Australian Information Commissioner (OAIC)
- Report to local police if you have evidence.
Scam support and recovery resources
- The MoneySmart website for financial recovery advice.
- ACSC for cybersecurity resources.
- Beyond Blue for mental health support.
- Financial Counselling Australia for free counselling.
- The Stay Smart Online program for threat updates and advice.
Basic protection measures we should all have in place
Here are simple yet effective steps to improve your online safety:
- Use strong, unique passwords and change them regularly.
- Enable two-factor authentication wherever possible.
- Keep software and operating systems updated.
- Install Sapher Shield to verify the authenticity of websites, links, and attachments before entering sensitive information.

